Introduction
Managing user accounts effectively is crucial for maintaining system security and efficiency in Linux environments. Whether you’re an IT professional, system administrator, or DevOps engineer, understanding Linux user management is essential. In this guide, we’ll explore creating and managing users in Linux, covering everything from basic user creation to advanced authentication methods like LDAP and PAM.
According to a recent study, misconfigured user permissions account for 35% of security breaches in corporate environments. Implementing proper user management practices can significantly reduce this risk.
Quick Answer Box
Creating and managing users in Linux involves using built-in commands to create, modify, and delete user accounts. It includes setting permissions, assigning user groups, and ensuring secure authentication mechanisms.
Key Takeaways:
- Use
useraddandusermodcommands for user creation and modification. - Assign users to groups for better permission management.
- Implement LDAP and PAM for centralized authentication.
- Regularly audit user accounts for security compliance.
- Secure root access to prevent unauthorized changes.
Understanding Linux User Management
What Are Linux Users?
Linux is a multi-user operating system, meaning multiple users can operate simultaneously. Each user has a unique UID (User ID) and specific permissions.
Types of Users in Linux
- Root User – Has unrestricted access and control over the system.
- Regular Users – Created for general system usage.
- System Users – Used for services and daemons (e.g., MySQL, Apache).
Creating a New User
The useradd command is used to create a new user in Linux.

-mcreates a home directory.-sassigns a shell (e.g.,/bin/bash).
Set a password using:

Modifying User Accounts
To modify an existing user, use usermod:
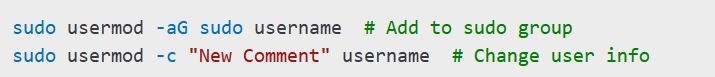
Deleting a User
To remove a user and their home directory:

Managing User Groups
Groups in Linux help manage permissions more efficiently.
Creating a new group:

Adding a user to a group:

Listing groups a user belongs to:

Advanced Authentication Methods
Using LDAP for Centralized Authentication
LDAP (Lightweight Directory Access Protocol) allows centralized user authentication across multiple systems.
- Install LDAP client:
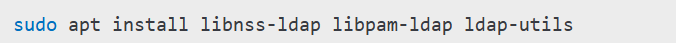
Configure /etc/nsswitch.conf and /etc/pam.d/common-auth to integrate LDAP authentication.
Implementing PAM (Pluggable Authentication Modules)
PAM provides dynamic authentication by supporting different authentication methods.
- To configure password policies, edit
/etc/security/pwquality.conf:

Best Practices for User Management
- Limit Root Access: Use
sudoinstead of direct root login. - Enforce Strong Password Policies: Use PAM modules to enforce complexity.
- Regularly Audit User Accounts: Run
lastlogandwhoto monitor activity. - Automate User Provisioning: Use Ansible or Shell scripting for bulk user management.
Did You Know?
Most Linux distributions store user account information in /etc/passwd, but passwords are stored securely in /etc/shadow, accessible only by root.
Important Note
Never disable root access entirely, as it may lock you out of your system. Instead, use sudo for privilege escalation and restrict direct root SSH login.
FAQs: Creating and Managing Users in Linux
1. What is the command to create a new user in Linux?
You can create a new user in Linux using the following command:
bashCopyEditsudo useradd -m username
The -m flag ensures that a home directory is created for the user.
2. How do I set a password for a new user?
Use the passwd command to set a password:
bashCopyEditsudo passwd username
You’ll be prompted to enter and confirm the new password.
3. What is the difference between useradd and adduser?
useraddis a low-level command with minimal default configurations.adduseris a user-friendly script that automatically sets up home directories and prompts for additional details.
4. How do I delete a user account?
To remove a user without deleting their home directory:
bashCopyEditsudo userdel username
To delete the user along with their home directory:
bashCopyEditsudo userdel -r username
5. How do I check the list of all users on my Linux system?
You can view all users by checking the /etc/passwd file:
bashCopyEditcat /etc/passwd
Or filter only usernames:
bashCopyEditcut -d: -f1 /etc/passwd
6. How can I add a user to the sudo group?
To grant a user administrative privileges, use:
bashCopyEditsudo usermod -aG sudo username
7. What is the difference between root and a regular user?
The root user has full administrative privileges and unrestricted system access.
Regular users have limited permissions and require sudo to execute administrative tasks.
8. How do I modify user details (like home directory or shell)?
Use the usermod command. For example:
- Change home directory: bashCopyEdit
sudo usermod -d /new/home/path username - Change default shell: bashCopyEdit
sudo usermod -s /bin/bash username
9. How do I create a group and add users to it?
Create a new group:
bashCopyEditsudo groupadd groupname
Add a user to the group:
bashCopyEditsudo usermod -aG groupname username
10. How can I see which groups a user belongs to?
bashCopyEditgroups username
or
bashCopyEditid username
11. How do I lock or unlock a user account?
To lock a user account:
bashCopyEditsudo passwd -l username
To unlock a user account:
bashCopyEditsudo passwd -u username
12. What is LDAP, and how does it help in user management?
LDAP (Lightweight Directory Access Protocol) is used for centralized authentication, making it easier to manage user access across multiple systems.
13. How can I check a user’s last login history?
bashCopyEditlast username
14. How do I enforce password expiration for security?
Set an expiration date for a user’s password:
bashCopyEditsudo chage -E YYYY-MM-DD username
To check current password aging settings:
bashCopyEditsudo chage -l username
15. What is the difference between /etc/passwd and /etc/shadow?
/etc/passwdstores user account details (username, UID, GID, home directory, shell)./etc/shadowstores encrypted passwords and password expiration details.
Conclusion
Effective user management in Linux is vital for security and system efficiency. By using proper tools and best practices, administrators can manage users effectively while reducing security risks.
Would you like to automate user management with scripts? Stay tuned for our next post on Linux automation with Ansible!
